For cybercriminals, every attack begins with a preparation phase. Doinmon records every moment of this critical setup process for you, revealing a threat's intent and readiness level long before it ever reaches your perimeter
How a "Harmless" Domain Registration Becomes a Weapon
When an attacker registers a domain that impersonates your brand, it's only the tip of the iceberg. The real danger emerges when this domain is "weaponized" for a phishing attack, a fake e-commerce site, or a Business Email Compromise (BEC) scam. This doesn't happen overnight; it's a deliberate, step-by-step process.
Here are the typical preparation steps an attacker takes:
- Step 1: Domain Registration
- It all starts with registering a convincing domain name that's easy to miss, like
yourcompany-support.comorc0mpany.com. This is the first signal.
- It all starts with registering a convincing domain name that's easy to miss, like
- Step 2: DNS Configuration
- To bring the domain to life, attackers configure its DNS records (A, MX, CNAME, etc.). Adding an MX record is one of the strongest indicators that they plan to send and receive emails from this domain—a clear sign of a potential phishing campaign. An A record points toward website setup.
- Step 3: Acquiring an SSL Certificate
- To build trust with victims, the fake site needs to start with
https. Attackers acquire an SSL certificate, often from free services like Let's Encrypt, to mark their site as "secure." This is a critical step that increases the severity of the attack.
- To build trust with victims, the fake site needs to start with
- Step 4: Website Cloning & Content Deployment
- In this phase, your actual website's login page, e-commerce checkout, or campaign landing page is copied and deployed to the malicious domain. The domain is now a visually active threat.
- Step 5: Setting Up Email Infrastructure
- If the goal is phishing, attackers set up the infrastructure to send mass emails from the malicious domain. This is the final sign that an attack is imminent.
How Doinmon Makes This Process Visible to You
Most security tools only see the final attack. Doinmon, on the other hand, provides you with a full intelligence briefing that begins the moment a threat is conceived. Our process turns ambiguity into clarity.
It starts with intelligent detection. Doinmon’s algorithms continuously scan for newly registered domains that impersonate or bear a suspicious resemblance to your brand assets. But detection is just the beginning.
The instant a suspicious domain is identified, it’s placed under continuous monitoring. We don’t just tell you it exists; we watch its every move. Doinmon begins to actively track critical properties like its DNS records (A, MX, CNAME), SSL certificate status, WHOIS data, and web page content. Each change is a clue, and we record all of them.
As these properties evolve, they feed our dynamic engine, which assigns a real-time Risk Score. A newly registered domain might start with a low score. However, when it suddenly activates an MX record for email and obtains an SSL certificate, its Risk Score escalates automatically, signaling a significant increase in intent and danger. This allows you to instantly prioritize the most imminent threats without manual analysis.
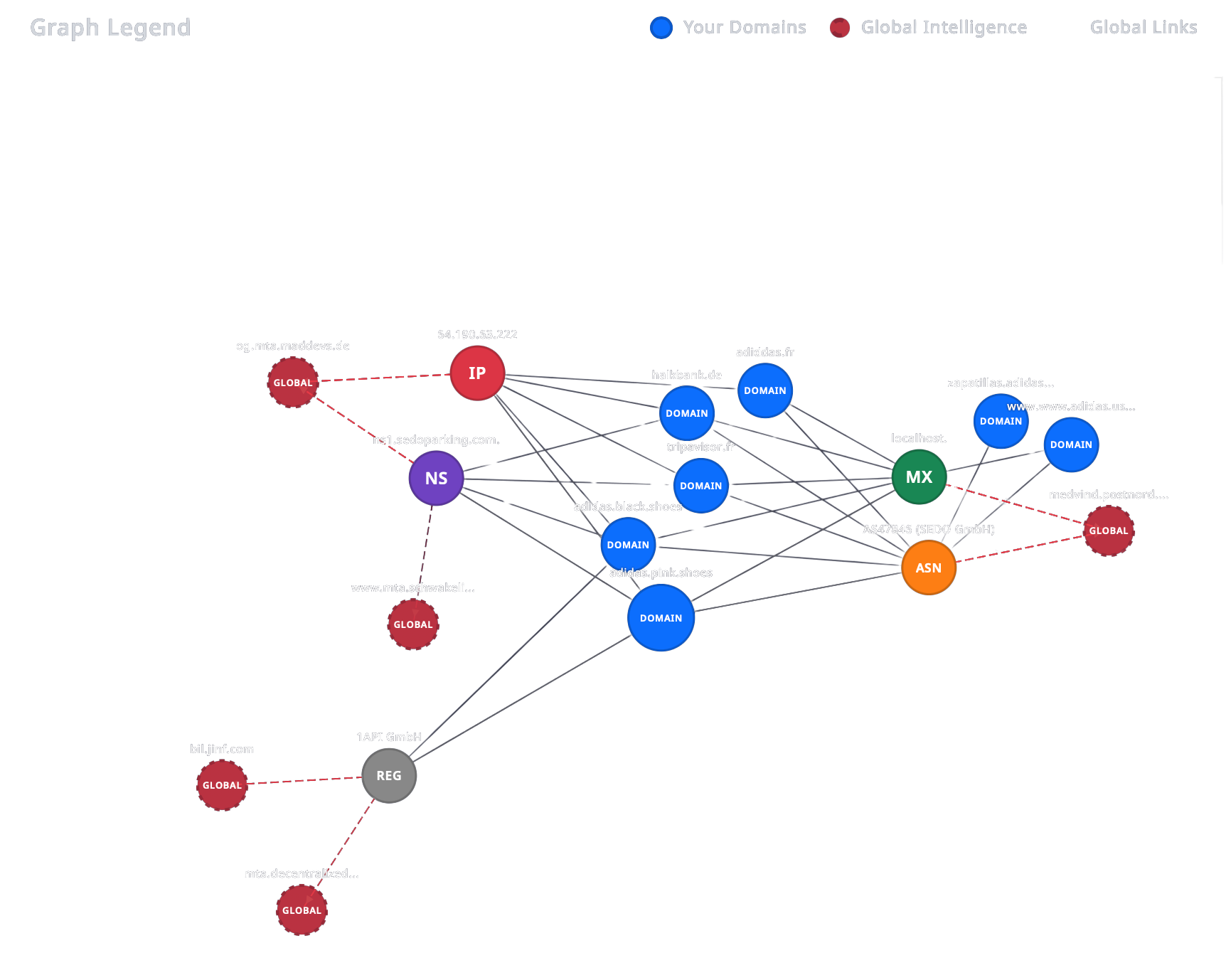
But what if this "new" threat isn't new at all? This is where Doinmon’s true power comes into play. Our Domain Intelligence module doesn't view this suspicious domain in isolation. It analyzes its digital DNA—the IP address it's hosted on, its nameservers, registrant details, and SSL certificate fingerprints—and cross-references this data against our extensive database of known malicious infrastructures.
Doinmon then visualizes these connections, creating a relationship map. You can see if your suspicious domain is linked to a known phishing operator, shares an IP with other fraudulent sites, or uses the same nameservers as a past attacker. Instead of just seeing a single risky domain, you see the entire potential campaign it belongs to, allowing you to understand the true scope of the threat and proactively defend against the attacker's entire network, not just a single domain
Why This Early Warning is Crucial
Monitoring the threat preparation phase gives you the power to be proactive, not reactive.
- Intervene at the Earliest Stage: You can contact the registrar or hosting provider to initiate a takedown request before the attack begins. The evidence collected by Doinmon (DNS records, SSL details, etc.) strengthens your case.
- Focus Your Resources: Your security team can stop chasing hundreds of "potential" risks and focus on the most "critical" threats that are in their final preparation stages.
- Protect Your Brand Reputation: By neutralizing the threat before a single phishing email reaches your customers or employees, you safeguard your brand's trust and integrity.
- Gain Contextual Intelligence: Instead of a simple "domain found" alert, you receive actionable intelligence: "This domain is impersonating your brand, has set up mail servers, and just activated an SSL certificate. It is preparing for an attack."
