In today's threat landscape, cybercriminals rarely operate in isolation. A phishing site is often just the tip of the iceberg, a single component of a larger, organized attack campaign. Without the right tools, seeing this bigger picture is nearly impossible. This is where Doinmon's automated domain intelligence and monitoring capabilities become a game-changer.
In this post, we'll demonstrate how Doinmon works through two distinct case studies. You'll see how two seemingly separate fake domains are connected to a more extensive, organized cyber campaign.
Case Study 1: From a Single Phish to a Coordinated Network
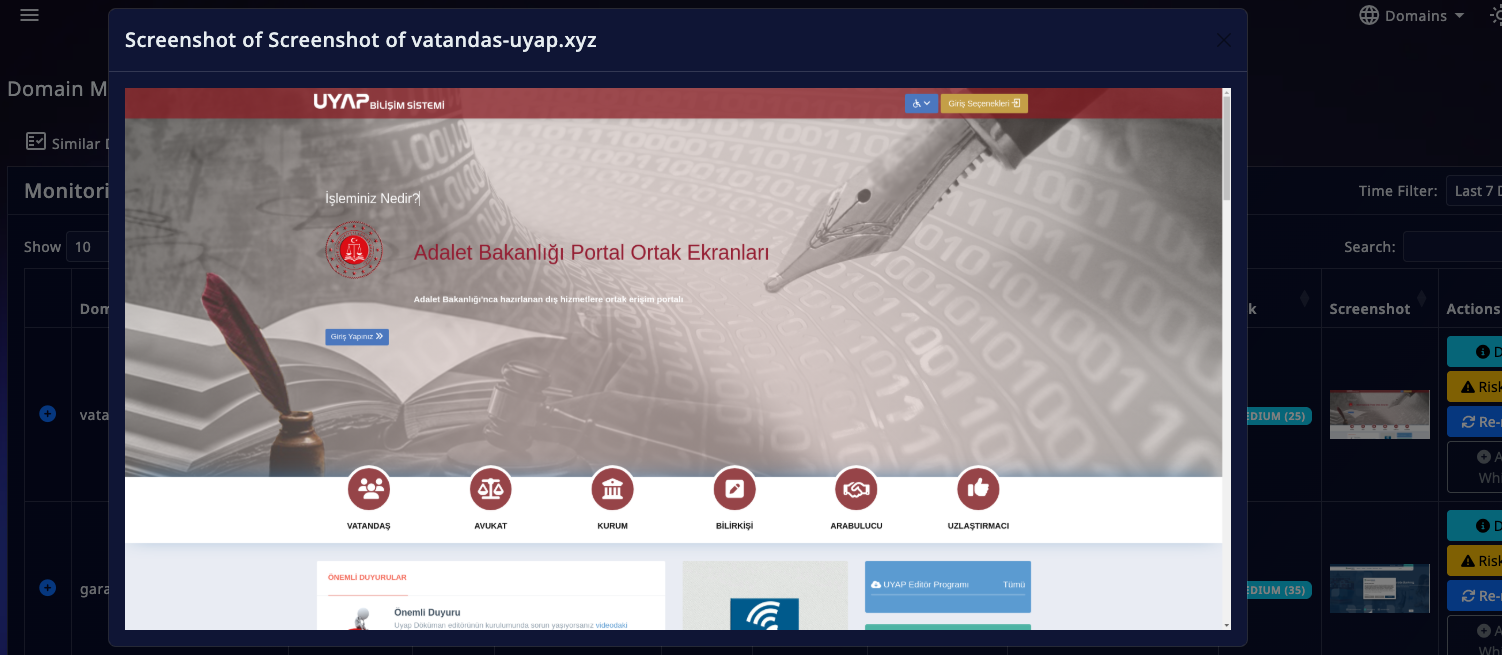
Our story begins with an alert from Doinmon's automated monitoring system. The system detected a fraudulent domain, "vatandas-uyap[.]xyz," impersonating a legitimate Turkish judicial portal. This site was a classic phishing attempt, designed to steal personal data.
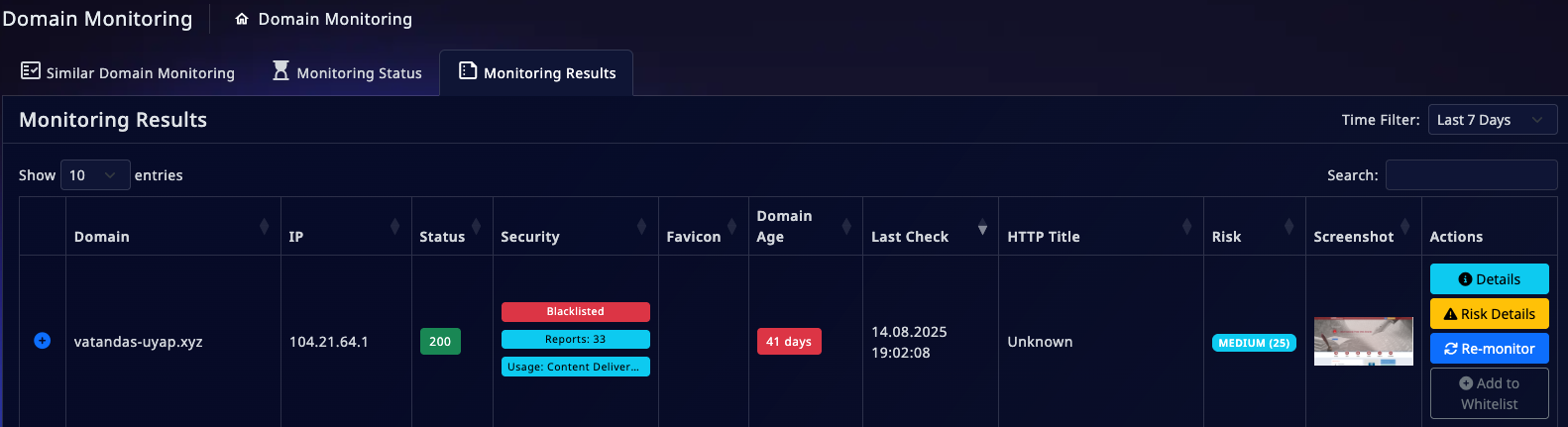
For a traditional cybersecurity analyst, this discovery would be the start of a manual, time-consuming investigation. However, Doinmon's automated monitoring system accelerates this process, reducing an analyst's workload by up to 90% and providing instant results.
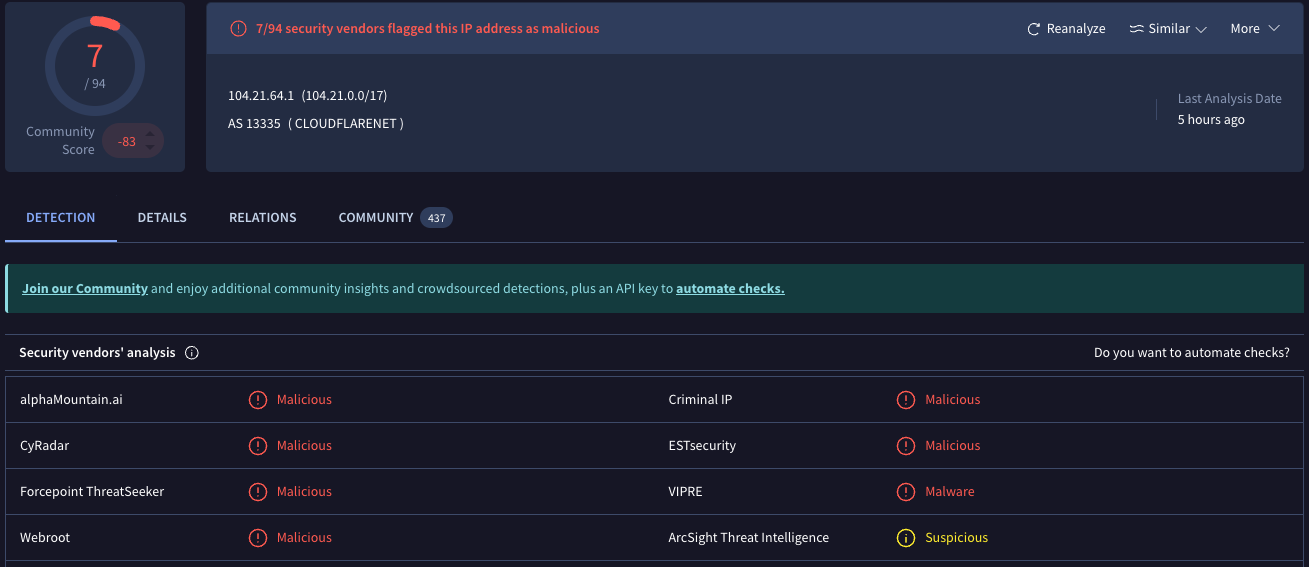
Using Doinmon's Relationship Analysis Module, our system automatically performed a 24/7 investigation that would have taken a security analyst weeks to complete, revealing the following:
- IP Address Connection: Doinmon automatically examined the IP address of vatandas-uyap[.]xyz. The system not only found that this IP was flagged as "suspicious" by reputable cybersecurity platforms like VirusTotal, but it also discovered another fraudulent domain—impersonating the major public enterprise Türkiye Petrolleri—was hosted on the same IP. Although this second site was protected by Cloudflare and its content couldn't be viewed, its connection to an active phishing threat immediately flagged it as a top-level risk.
- Registrar Connection: Our system delved deeper, analyzing the registrar used for these domains. It discovered the same registrar was also responsible for another imposter site, this one impersonating Trendyol, one of Turkey's largest e-commerce platforms. This third domain was actively redirecting users to a suspicious betting site.
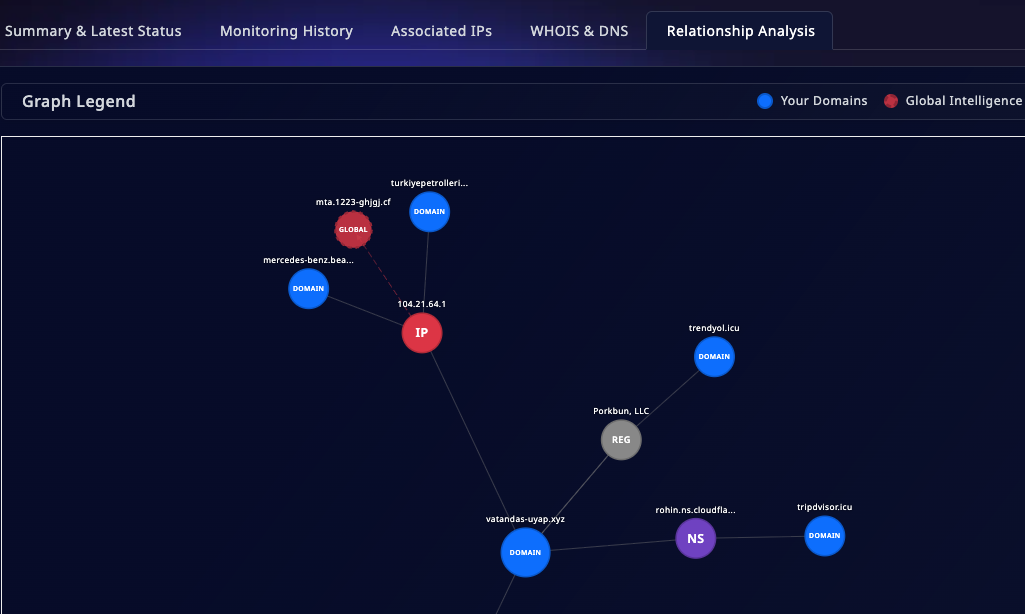
Conclusion: Doinmon's relationship analysis revealed that what appeared to be a single phishing site was actually part of a sophisticated, multi-pronged campaign targeting both the public and private sectors. With evidence from external sources like VirusTotal, Doinmon's analysis provided a clear understanding of the threat's true scope and intent.
Case Study 2: DNS Records and Naming Schemes Uncover a Hidden Link
This case study highlights a different aspect of Doinmon’s capabilities. The system detected "kgm-gov-tr[.]cc," a domain likely impersonating the Turkish General Directorate of Highways. Although the domain was only two days old and the websites themselves were not responding, Doinmon continued its analysis. A traditional tool might have dismissed the threat as "inactive," but our platform knows better.
Doinmon's analysis goes beyond simple content checks, delving into the deep technical characteristics of the domain:
- NS Server and Naming Impersonation: Doinmon determined that the domain's NS server was associated with the address "eusa[.]cc." This name strongly mimics Elektrik Üretim A.Ş. (EÜAŞ), a major public utility company in Turkey. This indicates that the attackers were deliberately using the names of public institutions to create a facade of legitimacy.
- ASN Connection: The analysis went even further, revealing that the site’s ASN (Autonomous System Number) was linked to another domain, "postnordinfo[.]cfd," which likely impersonates PostNord, a legitimate international logistics company.
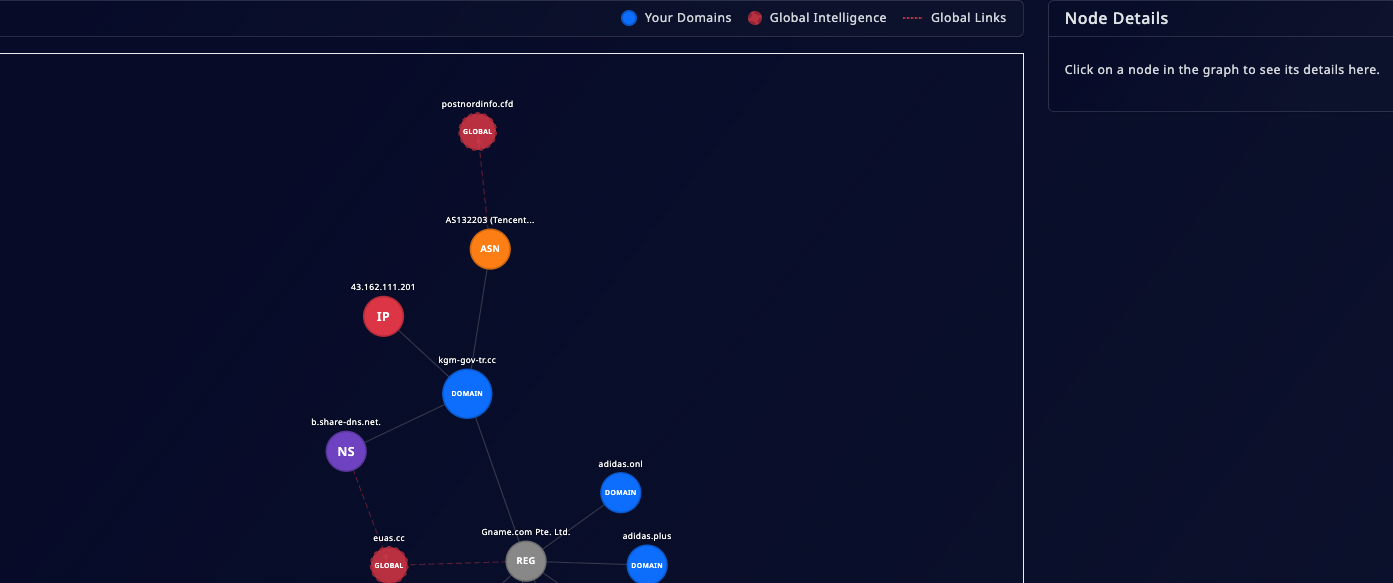
Conclusion: This case demonstrates that even when a website is unresponsive, technical data can provide powerful evidence of a threat. By connecting the "kgm-gov-tr[.]cc" domain to an EÜAŞ impersonator and an international brand imposter, Doinmon proved that the attackers were running a broad campaign without regard for sector, using different tactics to target multiple entities.
Beyond Traditional Methods: The Doinmon Difference
These two case studies clearly illustrate the complexity of modern cyber threats and why traditional methods fall short. Doinmon doesn’t just detect threats; it uncovers the organized networks, intentions, and potential impact behind them. By identifying these threats before they become fully operational, you can take proactive measures to protect your brand and reputation.
Are you ready to stop playing whack-a-mole with isolated threats? Doinmon's automated relationship and monitoring capabilities can help. Request a demo today to see how our platform can protect your brand's digital presence by revealing the hidden connections behind every threat.
